44 antivirus bypass techniques pdf
attack.mitre.org › techniques › T1105Ingress Tool Transfer, Technique T1105 - Enterprise | MITRE ... Adversaries may transfer tools or other files from an external system into a compromised environment. Tools or files may be copied from an external adversary-controlled system to the victim network through the command and control channel or through alternate protocols such as ftp. Computing Essentials 2021 [PDF] [73elth8nhsc0] - vdoc.pub E-Book Overview The rate of change in the digital information age is clearly increasing, and computer literacy is becoming a prerequisite. The goal of the 28th edition of Computing Essentials is to provide students with an introductory understanding of the concepts necessary for success and to instill an appreciation for the effect of information technology on people, privacy, ethics, …
Techniques - Enterprise | MITRE ATTCK® Enterprise Techniques Techniques represent 'how' an adversary achieves a tactical goal by performing an action. For example, an adversary may dump credentials to achieve credential access. ... Adversaries may build a container image directly on a host to bypass defenses that monitor for the retrieval of malicious images from a public registry.
Antivirus bypass techniques pdf
Check Point Security Appliance Brochure Prevention solution includes powerful security features such as firewall, IPS, Anti-Bot, Antivirus, Application Control, and URL ... the exploit phase, even before hackers can apply evasion techniques attempting to bypass the sandbox. Files are quickly Essential Eight Maturity Model - Cyber Microsoft Office macro antivirus scanning is enabled. Microsoft Office macro security settings cannot be changed by users. User application hardening Web browsers do not process Java from the internet. Web browsers do not process web advertisements from the internet. Internet Explorer 11 does not process content from the internet. Intrusion detection system - Wikipedia An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system.
Antivirus bypass techniques pdf. Penetration Testing | No Starch Press Penetration testers simulate cyber attacks to find security weaknesses in networks, operating systems, and applications. Information security experts worldwide use penetration techniques to evaluate enterprise defenses. In Penetration Testing, security expert, researcher, and trainer Georgia Weidman introduces you to the core skills and techniques that every pentester needs. mini cooper has no power - Czteryporydomu.pl Aug 02, 2017 · However, knowledge of the basic physical princi-ples underlying MRI acquisition is fundamental to image interpretation. This article, written for the general hospital physician, describes the basic physics of MRI taking into account the machinery, contrast weighting, spin- and gradient-echo techniques and pertinent safety issues.. chrome remote desktop curtain … en.wikipedia.org › wiki › Intrusion_detection_systemIntrusion detection system - Wikipedia A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system ... HowToRemove.Guide: No.1 Malware & Virus Removal Guides 1 day ago · EvilProxy phishing service allowing hackers bypass 2-Factor Authentication. September 7, 2022. ... The Gootkit Malware has resurfaced with updated techniques to compromise... August 1, 2022 ... Best Android Antivirus tools 2020. Reviews The Best Antivirus Apps iOS. Reviews Webroot WiFi Security VPN Review. Reviews
› en-us › advanced-research-centerTrellix Threat Center – Latest Cyberthreats | Trellix Register Now. September 27-29, 2022 ARIA Hotel & Casino Save the date and start planning to align with our leadership teams to learn our vision for a new kind of cybersecurity and learn more about our innovations in cyber intelligence and XDR architecture. en.wikipedia.org › wiki › MalwareMalware - Wikipedia Malware (a portmanteau for malicious software) is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive users access to information or which unknowingly interferes with the user's computer security and privacy. Essential Eight Maturity Model | Cyber.gov.au For example, these adversaries will likely employ well-known tradecraft in order to better attempt to bypass security controls implemented by a target and evade detection. This includes actively targeting credentials using phishing and employing technical and social engineering techniques to circumvent weak multi-factor authentication. en.wikipedia.org › wiki › CryptoLockerCryptoLocker - Wikipedia Operation. CryptoLocker typically propagated as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by a legitimate company. A ZIP file attached to an email message contains an executable file with the filename and the icon disguised as a PDF file, taking advantage of Windows' default behaviour of hiding the extension from file names to disguise the real .EXE ...
› searchsecurity › answersAnswers - IT and Computing - SearchSecurity - TechTarget The antivirus of yesteryear isn't a strong enough competitor to beat modern enterprise threats. Learn about the endpoint security features ready to tackle these battles head-on. Continue Reading. Attackers turn the tables on incident response strategies. Attackers expect incident response strategies and have a plan for when they encounter them. Unrestricted File Upload | OWASP Foundation Upload .rar file to be scanned by antivirus - command executed on a server running the vulnerable antivirus software; Attacks on other systems. Upload .exe file into web tree - victims download trojaned executable; Upload virus infected file - victims’ machines infected; Upload .html file containing script - victim experiences Cross-site ... veux-veux-pas.fr › en › classified-adsAll classifieds - Veux-Veux-Pas, free classified ads Website All classifieds - Veux-Veux-Pas, free classified ads Website. Come and visit our site, already thousands of classified ads await you ... What are you waiting for? It's easy to use, no lengthy sign-ups, and 100% free! If you have many products or ads, create your own online store (e-commerce shop) and conveniently group all your classified ads in your shop! Webmasters, you can add your site in ... Intrusion detection system - Wikipedia An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system.
Essential Eight Maturity Model - Cyber Microsoft Office macro antivirus scanning is enabled. Microsoft Office macro security settings cannot be changed by users. User application hardening Web browsers do not process Java from the internet. Web browsers do not process web advertisements from the internet. Internet Explorer 11 does not process content from the internet.
Check Point Security Appliance Brochure Prevention solution includes powerful security features such as firewall, IPS, Anti-Bot, Antivirus, Application Control, and URL ... the exploit phase, even before hackers can apply evasion techniques attempting to bypass the sandbox. Files are quickly










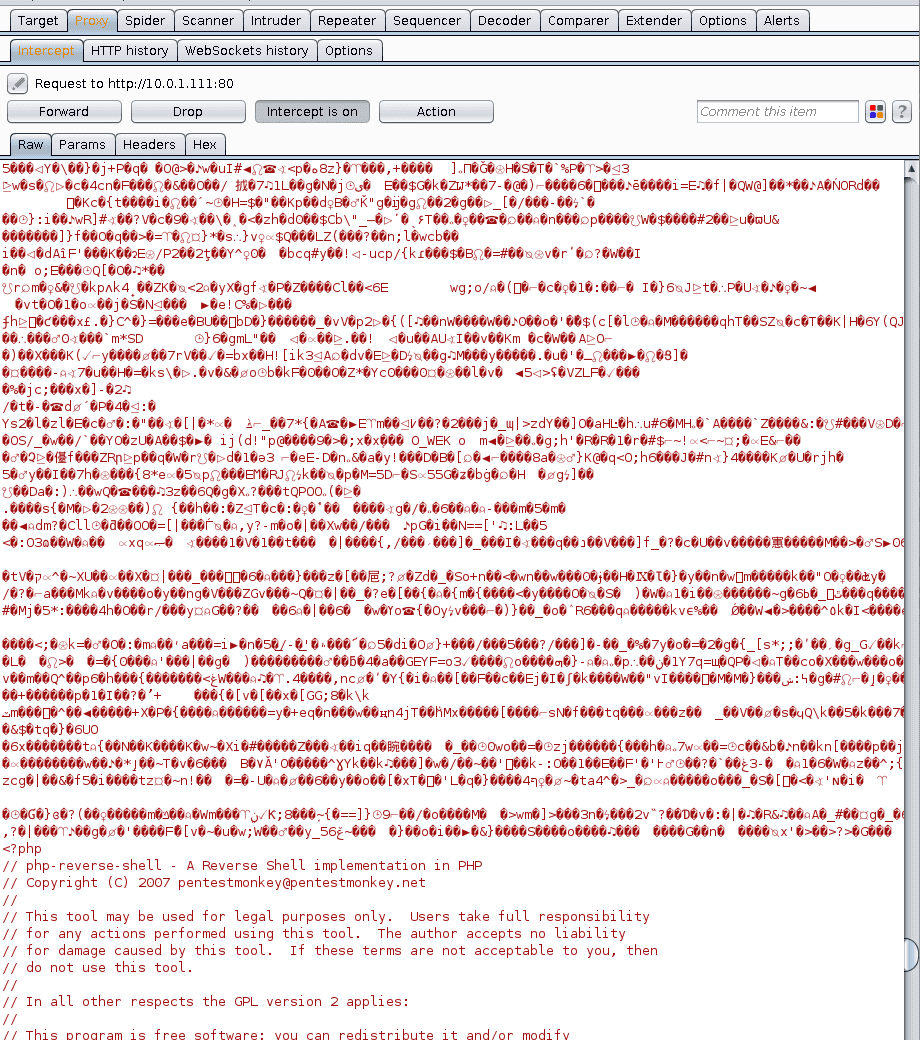



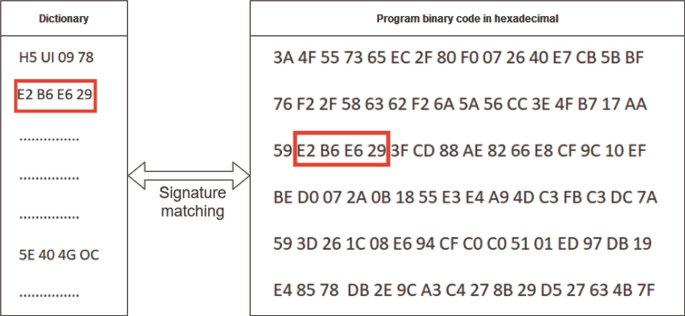

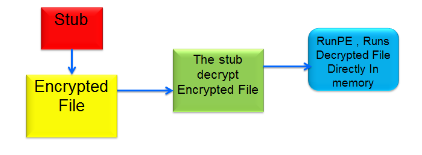







![√DOWNLOAD [PDF]> Antivirus Bypass Techniques: Learn ...](https://pbs.twimg.com/profile_images/1422390936387035136/CwjBvCoj_400x400.jpg)



![PDF] Bypassing Anti-Analysis of Commercial Protector Methods ...](https://d3i71xaburhd42.cloudfront.net/a729b493b108959702e778b13c36564f19c8f005/10-Figure15-1.png)
0 Response to "44 antivirus bypass techniques pdf"
Post a Comment