42 antivirus programming tutorial pdf
What Is Anti-Virus? - Roger Williams University Obtain anti-virus software only from known, trusted sources and vendors. It is a common ploy of cyber attackers to distribute fake anti-virus programs that are really malware. 2. Make sure you have the latest version of your anti-virus software installed, that your annual subscription is paid for and The Antivirus Hacker’s - ZenK-Security programming languages including writing scripts, doing web development, working with database design and programming, writing Windows device drivers and low-level code such as boot loaders or minimal operating systems, writing managed code, assessing software protections, and writing reverse-engineering and desktop security tools.
Pengertian Antivirus: Bagaimana Cara Kerja Perangkat ... Software antivirus bekerja untuk melindungi komputermu dan harus melakukan berbagai tindakan: melakukan pemindaian on-access, mencari ancaman yang tidak diketahui, melakukan pemindaian sistem lengkap, melakukan penghapusan malware, memasukkan file ke karantina, dan mengidentifikasi virus.
Antivirus programming tutorial pdf
PDF Cyber Security 101 - Carnegie Mellon University • Install and update your anti-virus and anti-malware with the latest security definitions • Create a unique user ID when sharing a computer with others • Enable pop-up blocker on your browser • Make an informed and rational decision prior to installing or downloading software on your computer • Lock your office when you leave Computer Security - Malwares - Tutorialspoint Computer Security - Malwares. In the previous chapter we treated antiviruses which helped us to protect our systems but in this chapter we will treat malwares, how to detect them manually, what are their forms, what are their file extensions, signs of an infected computer, etc. They are important to be treated because the infection rates of ... Types of Virus & Anti-virus - SlideShare Advantages of Anti-Virus Protecting Personal Information • Hackers and viruses go hand in hand. A good anti-virus program will protect you while you surf the Internet, preventing hackers from gaining access to personal things such as credit card information and bank account access. The firewall feature included with most anti-virus software ...
Antivirus programming tutorial pdf. Tutorial Jinni | Hub of Tutorials HermeticWiper Malware. Posted Under: Download Free Malware Samples , IOCs, Malware, Ukraine, Windows, Wiper, YARA on Feb 24, 2022. HermeticWiper is data and MBR Wiper that is being targeting Ukraine and is allegedly link to Russia. It intentionally cleans data on a device make it unrecoverable. It also deletes the MBR of the machine so that the ... Chapter 1: Introduction to Antivirus Software - The ... Chapter 1 Introduction to Antivirus Software. Antivirus software is designed to prevent computer infections by detecting malicious software, commonly called malware, on your computer and, when appropriate, removing the malware and disinfecting the computer.Malware, also referred to as samples in this book, can be classified into various kinds, namely, Trojans, viruses (infectors), rootkits ... Types of Viruses - Tutorialspoint.Dev Similar viruses install themselves in device drivers. Multipartite Virus : This type of virus is able to infect multiple parts of a system including boot sector,memory and files. This makes it difficult to detect and contain. Armored Virus : An armored virus is coded to make it difficult for antivirus to unravel and understand. PDF Java Web Programming with Eclipse - CSUSB An application programming interface (API) is a speci cation that de- nes how user code can access system functionality. The Java API refers to the speci cation that de nes how Java code may access functionality, such as opening a le in the le system, creating a socket connection with another process, creating a linked-list of objects, etc.
PDF Chapter 7 Software - FTMS • A presentation program is a software program that helps create a slideshow that addresses a topic. • Presentation programs are often used in businesses and schools for discussing a topic or for teaching. • It typically includes three major functions: - an editor that allows text to be inserted and formatted (PDF) Ethical hacking tutorial | gohel ashvin - Academia.edu Read Paper. PDF. Download Full PDF Package. f Ethical Hacking About this Tutorial Hacking has been a part of computing for almost five decades and it is a very broad discipline, which covers a wide range of topics. The first known event of hacking had taken place in 1960 at MIT and at the same time, the term "Hacker" was originated. Worm, Virus & Trojan Horse: Ethical Hacking Tutorial Worm, Virus & Trojan Horse: Ethical Hacking Tutorial. By Lawrence Williams. Updated February 19, 2022. Some of the skills that hackers have are programming and computer networking skills. They often use these skills to gain access to systems. The objective of targeting an organization would be to steal sensitive data, disrupt business ... Android Antivirus - Tutorials List - Javatpoint AVG antivirus is a robust antivirus software tool, developed by AVG Technology. It provides standard functions such as periodic scans, junk cleaner, Wi-Fi security, ram booster, power saver, call blocker, etc. Some important features of this Android antivirus are only available for a trial period of 14 days. It has few add-on apps such as AVG ...
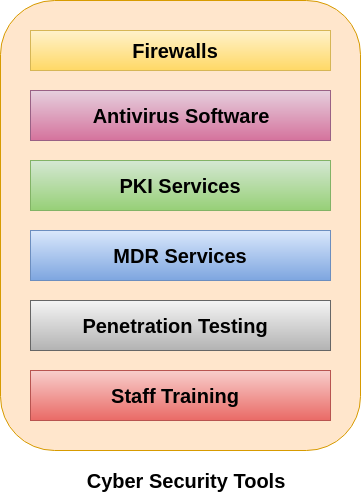
How to Download and Install Avast! Free Antivirus (with ... Open Avast. If Avast doesn't open immediately after installing, double-click its icon on the Windows desktop. Alternatively, you can click the Start menu and type avast into Start, then click the "Avast Free Antivirus" app icon in the Start menu.. On Mac, open a new Finder window, click Go in the menu bar at the top and then click Applications in the drop-down menu. How to Make an antivirus engine | Tutorial • Adlice Software When roaming around the techies forums, I often see some people (and many not very experienced)asking for “How do I make an antivirus”, sometimes with not very adapted languages (bat, PHP, …) and having a wrong idea of what an antivirus is, and how it should be built. I’ve also seen many “Antivirus softwares” made by kiddies, with very few still-at-school people and about 4 hours per day of coding on several weeks. I’m not telling kiddies are not skilled, but I’m telling building an antivirus engine needs either lot of skilled people with full time job plus lot of time to release a decent software or lot of money to pay them 🙂 (in case they are not volunteer). So, I’ll cover here the guidelines for a basic antivirus coding, for Windows and in C/C++. One can found here the pointers to design an antivirus engine, or simply learn how most of them are built. Tutorials - TotalAV Jan 27, 2021. In late 2020, TotalAV developed and refined its ad blocking service which operates via browser extensions for Chrome, Firefox and Edge. Users will be familiar with TotalAV's Safe Site browser extension, which has a feature within it called Ad Block Pro. Now, all TotalAV customers who have this addon can benefit from a dedicated ... Cyber Security Tools - Tutorials List - Javatpoint Antivirus software is a program which is designed to prevent, detect, and remove viruses and other malware attacks on the individual computer, networks, and IT systems. It also protects our computers and networks from the variety of threats and viruses such as Trojan horses, worms, keyloggers, browser hijackers, rootkits, spyware, botnets ...
PDF IT 1500 Final Exam Introduction to ... - JustAnswer An antivirus program An audio/sound card A memory storage device 13 Select the true statement about a mouse. It is an input device that enables users to enter text or number sequences into a computer. It is an input device that converts images or text into digital information.
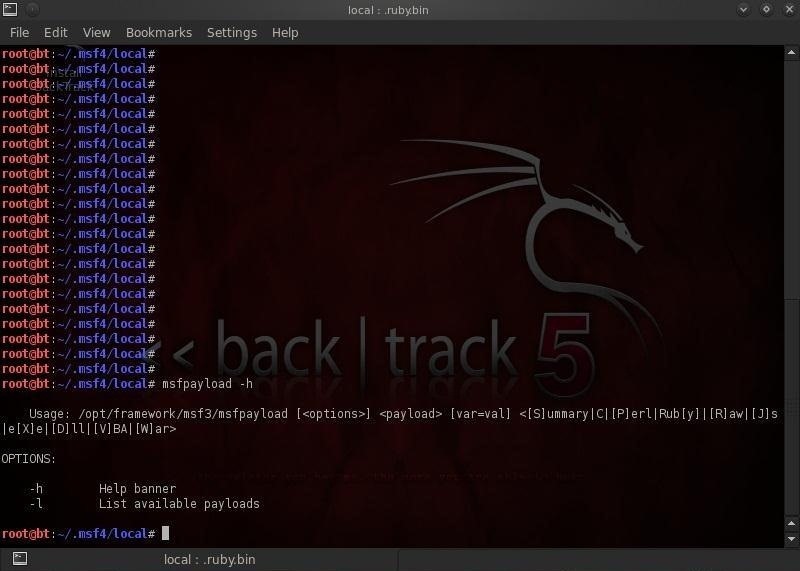
(PDF) Guide To Kali Linux.pdf | Muhammad Andyk Maulana ... K ali Linux is the latest linux distribution made curity tools. Kali Linux is designed to support both for penetration testing by and used by secu- 32-bit and 64-bit platform and ARM Architecture. rity assessors and hackers. Kali Linux is al- so considered as a successor to Backtrack.
PDF Introduction to Computer Security anti-virus and anti-spyware software ! Don't click on unknown or unsolicited links or attachments, and don't download unknown files or programs onto your computer or other devices . 15 Key steps, continued (2 of 2):! Remember that information and passwords sent via
PDF avast! antivirus Installation Guide This will allow you to get avast! antivirus updates for the duration of the license you purchased. avast! Home Edition users must re-register again after one year to continue getting the updates. The first steps are now completed and you have a running version of avast!, please see the program help file for further instructions on the usage of ...
Computer Virus - W3schools Online Programming Tutorials In 1971, Bob Thomas of BNN technologies wrote a program, 'Creeper System' - a self-replicating program to test Jon von Neumann's theory, which was published as an article in 1949. Since 1987- when a virus infected ARPANET, a vast network used by the Department of Defense and many universities, many antivirus programs were developed, which ...
How to Develop Computer Virus using C? - Code with C Save and close all the important programs and run .exe file of this program; it will restart your system. The source code has been compiled in Code::Blocks using GCC compiler. If you want to develop this computer virus using C source code compiled in Turbo C, run the .exe file of the code below after compiling it in Turbo C.
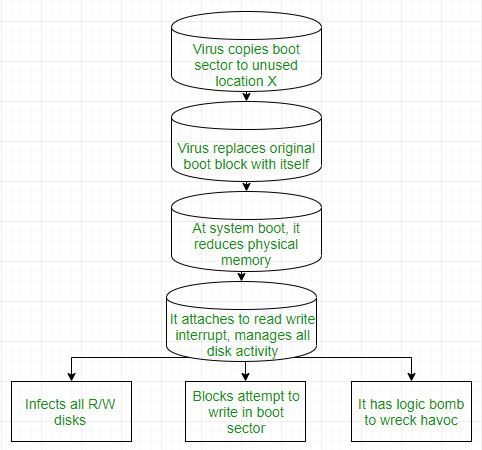
PDF Lesson 6: Hacking Malware - Hacker Highschool several segments. The first virus segment would be a harmless PDF but inside the PDF was a scripting call to perform a download of some more of the virus. The second portion of the virus is encrypted so malware detectors don't notice the install. The creators think of ways to make a virus look anything but like a virus. Since antivirus
XAMPP Tutorial: how to create your own local test server ... XAMPP is the title used for a compilation of free software.The name is an acronym, with each letter representing one of the five key components. The software packet contains the web server Apache, the relational database management system MySQL (or MariaDB), and the scripting languages Perl and PHP.The initial X stands for the operating systems that it works with: Linux, Windows, and Mac OS X.
Audience - Tutorialspoint In this tutorial, we will treat the concept of Computer Security which can be a laptop, a workstation, a server or a network device. This tutorial is done mainly for people that are ... a Kaspersky antivirus being updated. Computer Security 7 Check for the unusual services running that consumes resources.
N00NY/Antivirus-Python- - GitHub Antivirus-Python-. This is a project I started at the beginning of December 2017. I was simply bored out of my mind and needed a good topic for a term paper for school, so yeah here it is. Since then it has gone from a console application to an "acceptable" GUI. This antivirus script is signature based only at the moment.
(PDF) An introduction to computer viruses: Problems and ... A set of malicious programming code, scripts, active content, or intrusive software that is designed to destroy intended computer systems and programs or mobile and web applications is referred to ...
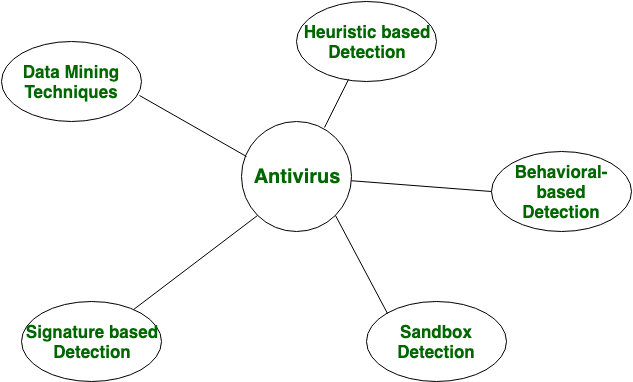
(PDF) How Anti-virus Software Works?? - ResearchGate For e.g. if an antivirus program notice s that a program is trying to open every E XE file on your computer and infecting it by writing a copy of the original program into it. So an antivirus p ...
Types of Virus & Anti-virus - SlideShare Advantages of Anti-Virus Protecting Personal Information • Hackers and viruses go hand in hand. A good anti-virus program will protect you while you surf the Internet, preventing hackers from gaining access to personal things such as credit card information and bank account access. The firewall feature included with most anti-virus software ...
Computer Security - Malwares - Tutorialspoint Computer Security - Malwares. In the previous chapter we treated antiviruses which helped us to protect our systems but in this chapter we will treat malwares, how to detect them manually, what are their forms, what are their file extensions, signs of an infected computer, etc. They are important to be treated because the infection rates of ...
PDF Cyber Security 101 - Carnegie Mellon University • Install and update your anti-virus and anti-malware with the latest security definitions • Create a unique user ID when sharing a computer with others • Enable pop-up blocker on your browser • Make an informed and rational decision prior to installing or downloading software on your computer • Lock your office when you leave
























![Top 6 Free Antivirus Apps for Windows Phone[2021]](https://mobiletrans.wondershare.com/images/en/phone-transfer/top-6-free-antivirus-apps-for-windows-phone-4.jpg)
0 Response to "42 antivirus programming tutorial pdf"
Post a Comment