39 g data antivirus proxy service cpu
25+ Bootable Rescue Disks of All Major Antivirus: Free ... To create Avast rescue disk, open Avast antivirus in malware-free system, navigate to Tools >> Rescue disk. Now, follow the instruction to burn Avast rescue disk in CD or USB. 6. AVG Rescue CD AVG Rescue CD is text-based tool which even scans archive to remove virus. G Data Antivirus Proxy Service Cpu G Data Antivirus Proxy Service Cpu squid proxy two network cards, what is business service and proxy service in osb nginx proxy set header x forwarded for wmi win32 product, epoxy flooring garages g pro hero wired weight.
Sizing considerations - Sophos The EAS proxy does not require a lot of CPU or memory, but its key limitation is bandwidth. As the EAS proxy is critical for the delivery of email, for large installations, we recommend you use multiple instances of EAS proxies behind a load balancer. Note that this setup is not required for the PowerShell mode.

G data antivirus proxy service cpu
Symantec Norton Antivirus : List of security vulnerabilities The POP3 proxy service (POPROXY.EXE) in Norton AntiVirus 2001 allows local users to cause a denial of service (CPU consumption and crash) via a long username with multiple /localhost entries. 17 CVE-2000-0477: DoS Overflow 2000-06-14: 2017-10-10 nifi.apache.org › docs › nifi-docsNiFi System Administrator’s Guide Jan 13, 2022 · The other two scenarios are when the request is proxied. This could either be proxied by a NiFi node (e.g. a node in the NiFi cluster) or by a separate proxy that is proxying a request for an anonymous user. In these proxy scenarios nifi.security.allow.anonymous.authentication will control whether the request is authenticated or rejected. In ... pc is very, very slow, suddenly - Computer Hope Windows 7 Basic should be the only one running for an Intel Atom processor. Running anything higher than the Basic is not a good idea. Processor speed is fine, but the way Windows threads objects in versions higher than Basic cannot be handled by an Intel Atom processor.
G data antivirus proxy service cpu. › it-glossaryIT Terms Glossary | Information Technology Definitions ... Refers to: 1) a program that has the function of translating data into a different format (e.g., a program used to import or export data or a particular file); 2) a pattern that prevents non-matching data from passing through (e.g., email filters); and 3) in paint programs and image editors, a special effect that can be applied to a bit map. G Data CPu Auslastung dauerhaft bei 50%. Woran liegt das ... G Data CPu Auslastung dauerhaft bei 50%. Woran liegt das? Die CPU Auslastung des Programmes GData, bzw des Prozesses AVKTray.exe liegt dauerhaft bei 50% (+-10) und das sorgt oft dafür, das der PC überlastet ist und andere Programme anfangen, abzustürzen. Ich habe GData schon lange, doch heute ist die Auslastung dauerhaft so hoch. tmproxy.exe - What is tmproxy.exe? - ProcessLibrary.com In Windows Task Manager, you can see what CPU, memory, disk and network utilization is causing the PC-cillin 2003 antivirus process. To access the Task Manager, hold down the Ctrl + Shift + Esc keys at the same time. These three buttons are located on the far left of your keyboard. tmproxy.exe docs.fortinet.com › document › fortigateCLI Reference | FortiGate / FortiOS 7.0.3 | Fortinet ... FWF_61F: a WiFi/desktop model with 10x GE RJ45 ports (including 7x Internal Ports, 2x WAN Ports, 1x DMZ Port), Wireless (802.11 a/b/g/n/ac-W2), 128GB SSD onboard storage. FGT_501E: a mid-range model with 2x 240GB SSD storage, NP6 and CP9 acceleration, 2x 10GE SFP+ slots, 8x GE SFP slots and 10x GE RJ45 ports.
Setup Instructions and Troubleshooting - Cloudamize Support To use a proxy server, enable "Use proxy" and type in HTTPS proxy and port. If your proxy server needs user credentials, enable "Use proxy credential" and enter the Username and Password. Click "Next". Click Install to begin the Cloudamize Agentless Data Collector installation Once the installation completes, click Finish to close the installer PDF Sophos Mobile The internal EAS proxy is recommended for installations with no more than 500 devices syncing emails and if no failover or clustering is required. The standalone or external EAS proxy is recommended for larger installations, if device management and email proxy have to separate or clustering is required. Zimbra Collaboration Performing a Single-Server Installation The Zimbra MTA also includes anti-virus and anti-spam components. Zimbra Proxy: Zimbra Proxy is a high-performance reverse proxy service for passing IMAP[S]/POP[S]/HTTP[S] client requests to other internal Zimbra Collaboration services using nginx. This package is normally installed on the MTA server(s) or on its own independent server(s). Sizing a Backup Proxy · Veeam Best Practices Guide V9 U1 A task processes 1 VM disk at a time and CPU/RAM resources are used for inline data deduplication, compression, encryption and other features that are running on the proxy itself. In the User Guide it is stated that proxy servers require 2 GB RAM + 500 MB per task. Please consider these values as minimum requirements.
Sizing a Backup Proxy · Veeam Best Practices Guide V9 A task processes 1 VM disk at a time and CPU/RAM resources are used for inline data deduplication, compression, encryption and other features that are running on the proxy itself. In the User Guide it is stated that proxy servers require 2 GB RAM + 500 MB per task. Please consider these values as minimum requirements. PDF G DATA Business solutions V. 14.2.0 Changelog This document lists the changes that were introduced in version 14.2.0 of G DATA Business Solutions. To ensure relevance and readability, this document lists only major features and improvements. This document applies to the following products: G DATA Antivirus Business, G DATA Client Security Business, G DATA Endpoint Protection Business, G ... Q&A - G-Data is using a load of RAM. | MalwareTips Community May 28, 2020 — GData it's more lighter than the past. Maybe he's monitoring a suspicious process or program running in your computer?20 posts · Well, I saw many of you guys saying that G-Data got very light over the years and that ur ...Missing: proxy | Must include: proxy › blogBlogs - ZDNet ZDNet's technology experts deliver the best tech news and analysis on the latest issues and events in IT for business technology professionals, IT managers and tech-savvy business people.
CrowdStrike FAQs | University IT - Stanford University --apd: the sensor's proxy status (enabled or disabled) (This is only applicable if your host is behind a proxy server) --aph: the sensor's proxy host --app: the sensor's proxy port --version: the sensor's version number . The sensor requires these runtime services: network . systemd . local-fs . sysinit . multi-user . shutdown . Verifying the ...
docs.fortinet.com › document › fortigateExplicit web proxy | Cookbook - Fortinet Jun 02, 2010 · Explicit web proxy. Explicit web proxy can be configured on FortiGate for proxying HTTP and HTTPS traffic. To deploy explicit proxy, individual client browsers can be manually configured to send requests directly to the proxy, or they can be configured to download proxy configuration instructions from a Proxy Auto-Configuration (PAC) file.
windowsreport.com › blue-yeti-not-recognizedBlue Yeti mic not recognized in Windows 11? Try these fixes Jan 05, 2022 · Users have reported their Blue Yeti mic is not recognized by their system, nor in the Logitech G Hub program, and wrong hardware settings could be to blame. Out of date drivers often are at the root of the problem, but you'll discover the appropriate tool for the job in this article.

Qotom-Q190G4N-S07 Quad-Core Mini Computer Barebones with WiFi System Intel Celeron J1900 Small Fanless Mini PC
appuals.com › localservicenonetworkfirewall-highWhat is 'LocalserviceNoNetworkFirewall' and How to Fix its ... Jan 31, 2022 · The high CPU usage by the LocalserviceNoNetworkFirewall could be a temporary glitch of the Windows Firewall and restarting the same may solve the problem. Right-click Windows and open Task Manager. Open the Task Manager from the Quick Access Menu; Now head to the Services tab and right-click on WinDefend (Microsoft Defender Antivirus Service).
AVKProxy.exe Windows process - What is it? The company is best known for being one of the first developers of an anti-virus program which was written for ATARI. G Data was founded in 1985 by Kai Figge and Frank Kühn, and is currently headquartered in Bochum, Germany. AVKProxy stands for AntiVirus Kit Proxy Service. The .exe extension on a filename indicates an exe cutable file ...
Configure device proxy and Internet connection settings ... Open MDEClientAnalyzerResult.txt and verify that you've performed the proxy configuration steps to enable server discovery and access to the service URLs. The tool checks the connectivity of Defender for Endpoint service URLs. Ensure the Defender for Endpoint client is configured to interact.
AVKProxy.exe Windows Prozess - Was ist das? - file Dieses offene Datei Informationsforum hilft Ihnen, wenn Sie wissen möchten, ob die Datei unnötig oder sogar schädlich ist bzw. wie Sie AVKProxy.exe Fehler beseitigen oder die zugehörige G Data AntiVirus Proxy Dienst Software deinstallieren. Hier klicken, um einen Gratis Scan nach AVKProxy.exe Fehlern zu starten AVKProxy.exe Datei Info
G DATA AntiVirus The most important feature of the G DATA AntiVirus Management Server is its ar- ... computer with only one central processing unit (CPU)) at a single ...80 pages
CPU usage very high, drops to normal as i open task ... The cpu usage stays very high (>80%) even when idle or during normal web surfing. When I open task manager to see whats the problem, it drops to normal levels (<10%). It is probably because of a malware. I've tried malwarebytes, but it does not detect any malware. Please help Thanks
linux - vmlinuz process runs on 100% CPU - Stack Overflow The confluence user running the /boot/vmlinuz process and it eats the CPU. If I kill -9 this process it starts again a few seconds later. After reboot the VPS: Confluence and Jira started automatically. Confluence is running a few seconds correctly then something kills the process. The Jira process is still running.
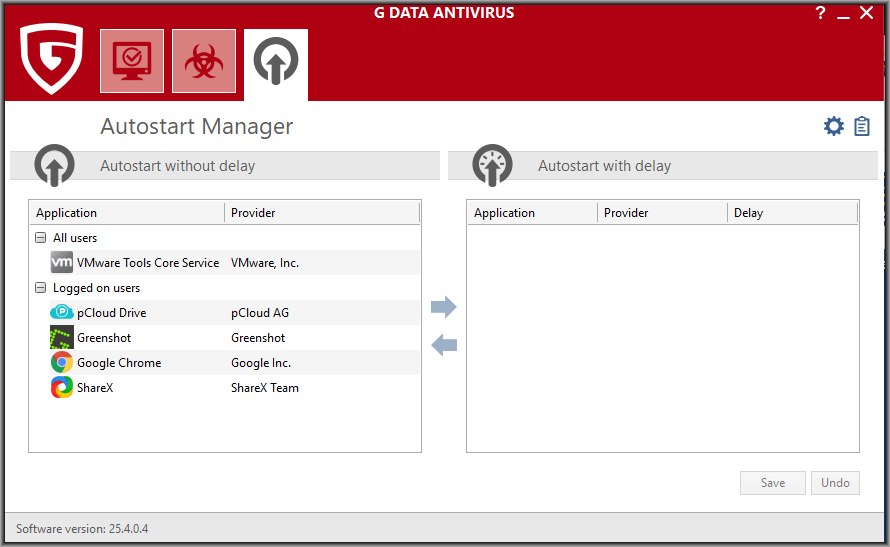
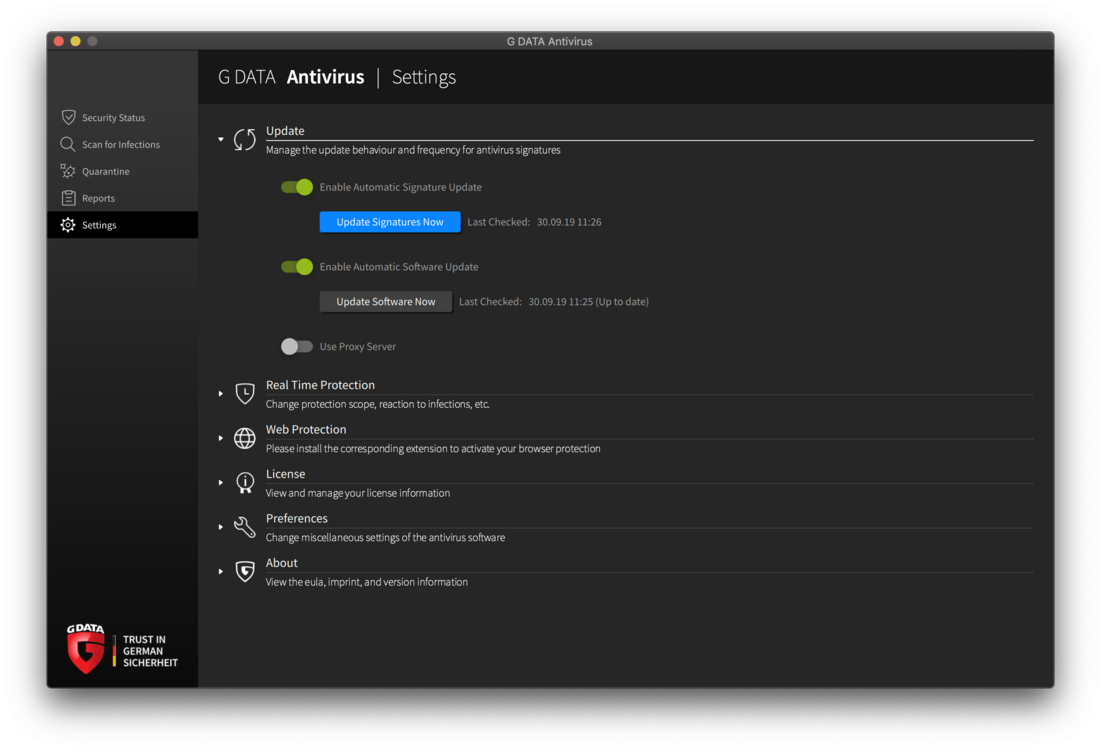
SecurityCenter > CPU-Last G Data InternetSecurity Navigation: SecurityCenter > CPU-Last Unter der Beschriftung G Data sehen Sie die aktuelle Auslastung Ihres Computers durch die Software. Darunter - unter der Beschriftung System - die momentane Gesamtauslastung Ihres Rechners.
Authentication Proxy - FAQ and Troubleshooting | Duo Security Can the Proxy be configured for multiple Duo applications? Yes. You can specify multiple server sections in the configuration file. Each will have a different ikey and skey. If the server sections are the same type, append a number to the section name — e.g. [radius_server_auto2] and use a distinct port number for each.
How to detect antivirus installed on windows 2003 server ... 0, // Authority (e.g. Kerberos) 0, // Context object &pSvc // pointer to IWbemServices proxy ); But in case of windows 2003 server and 2008 server 2003 server R2and 2008 server R2 these above namespace are not present so this is not working there.

ASUSTOR AS6602T Lockerstor 2-Bay NAS Enclosure (No Drives), Quad Core CPU, 4GB DDR4, USB 3.2, 2 x 2.5G LAN, 2 x M.2 NVMe
Antivirus | Administration Guide * Proxy mode antivirus inspection on CIFS protocol has the following limitations: Cannot detect infections within some archive files. Cannot detect oversized files. Other antivirus differences between inspection modes Starting from 6.4.0, the scan mode option is no longer available for flow-based AV.
Official docker images of clamav - docker-clamav to use it via a REST proxy like @solita made clamav-rest or to check files on a server via e.g. node.js kylefarris/clamscan to directly connect to clamav via TCP port 3310 ClamAV daemon as a Docker image.
Microsoft signed a malicious Netfilter rootkit | G DATA Microsoft signed a malicious Netfilter rootkit. 06/25/2021. G DATA Blog. What started as a false positive alert for a Microsoft signed file turns out to be a WFP application layer enforcement callout driver that redirects traffic to a Chinese IP.
McAfee Scanner Service in Task Manager showing high CPU Usage Try to boot the computer in Safemode and check the CPU and Memory usage of McAfee service. Perform a McAfee update when the computer is in safemode, reboot the computer in normal mode and perform a windows update and restart the computer again to check the computer performance. 0 Kudos Share Reply xboxerj Level 9 Report Inappropriate Content
Cookbook | FortiGate / FortiOS 6.2.10 | Fortinet ... CPU usage and packet loss. Traffic scanned on the one-arm sniffer interface is processed by the CPU, even if there is an SPU, such as NPU or CP, present. The one-arm sniffer may cause higher CPU usage and perform at a lower level than traditional inline scanning, which uses NTurbo or CP to accelerate traffic when present.
Kerio Connect Server is not responding, Internet ... Check your Internet connection ' error. As a result, the email system may experience intermittent load, transfer, and bandwidth usage problems. For short periods of time, HTTPS service may produce permanent data transmission. As an outcome, email clients such as Webmail can return network timeout pages. Prerequisites
G DATA Business Solutions Reference Guide If the existing mail server can deal with the CPU and RAM load, installing MailGateway on ... Client; G DATA Internet Security for Android; Subnet server).176 pages
svchost.exe(Network Service) killing my CPU/Internet ... Option 2: Turn off the DNS Client Service (in your list of services), and reboot. If you turn that service off, you won't be able to resolve DNS names on your local network, but most people don't ...
pc is very, very slow, suddenly - Computer Hope Windows 7 Basic should be the only one running for an Intel Atom processor. Running anything higher than the Basic is not a good idea. Processor speed is fine, but the way Windows threads objects in versions higher than Basic cannot be handled by an Intel Atom processor.
nifi.apache.org › docs › nifi-docsNiFi System Administrator’s Guide Jan 13, 2022 · The other two scenarios are when the request is proxied. This could either be proxied by a NiFi node (e.g. a node in the NiFi cluster) or by a separate proxy that is proxying a request for an anonymous user. In these proxy scenarios nifi.security.allow.anonymous.authentication will control whether the request is authenticated or rejected. In ...
Symantec Norton Antivirus : List of security vulnerabilities The POP3 proxy service (POPROXY.EXE) in Norton AntiVirus 2001 allows local users to cause a denial of service (CPU consumption and crash) via a long username with multiple /localhost entries. 17 CVE-2000-0477: DoS Overflow 2000-06-14: 2017-10-10













0 Response to "39 g data antivirus proxy service cpu"
Post a Comment